Setup yor LAN or wireless network to interconnect your local area connectivity and internet.
Network Security
Build your own network and connected to the world securely.
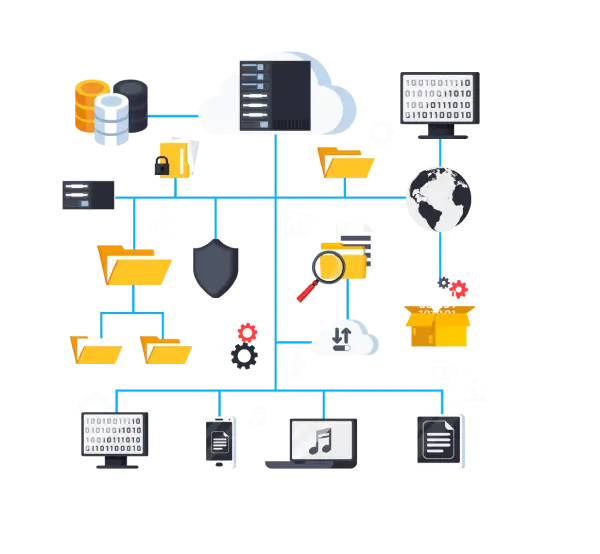
Setup your own network for sharing, communicate and for many resources. You may access your network by a client system from a dedicated server. Security will also protect your private network with advanced technology such a cyber security.

A computer network is a group of computers that use a set of common communication protocols to sharing resources
A client-server network is the medium through which clients access resources and services from a central computer system or host.
Network security is any activity designed to protect your network & data and provided to a network from unauthorized access and risks.
Networking & Security
Commputer Network About Our Company?

A computer network is a set of computers connected together for the purpose of sharing resources. The most common resource shared today is connection to the Internet. Other shared resources can include a printer or a file server. The Internet itself can be considered a computer network.

Our Benefits
Get More Benefit with Our Networking Services
Router will connect over internet
Create, publish, and promote engaging content to generate and build a dedicated community.
We select themed keywords based on user-intent to solidify rankings based on what users searches

Wilcoxon
We’re Best Insurance Company
Pricing Package
Choose Flexible Pricing Plan
Server Client
Server Client Network Solutions
A major advantage of the client-server network is the central management of applications and data. The client-server model has become one of the central concepts used in network computing. and it is a distributed application structure that partitions tasks or workloads to fat clients.
Our Benefits
Get More Benefit with Our Server Client
Windows and Linux server installation and configaration with fully server-client setup
All clients are managed by server permission like login, limited space & browse, log maintain etc.
This server genarelly used for getting client logs, security over internet and redirect your client browser access.
Your client always login with tour domain system and you can get all logs from your client system.

Wilcoxon
We’re Best Insurance Company

Pricing Package
Choose Flexible Pricing Plan
Network Security
Professional Security With Advanced Technolgy

Network security is important for home networks as well as in the business world. A solid network security system helps reduce the risk of data loss, theft and sabotage.


Our Benefits
Protected Network Security
Firewall device monitors and filters incoming and outgoing network traffic based on security policies
Software analyses network traffic patterns, monitors bandwidth, and helps identify unwanted traffic.
This process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems.
Network security is any activity designed to protect the usability and integrity of your network and data.


Wilcoxon
We’re Best Insurance Company

Pricing Package
Choose Flexible Pricing Plan
We Offers
What We Offer About Security
1
Network security is the process of taking physical and software preventative measures to protect the underlying networking infrastructure from unauthorized access.
2
Data Security is a process of protecting files, databases, and accounts on a network by adopting a set of controls, applications, and techniques.
3
Artificial intelligence (AI) and machine learning (ML) technologies will be critical in solving many of today's complex network and business problems in real time.


Network Security
Provide Advanced Security For Advanced Threats.
There are three components of network security: hardware, software, and cloud services. Hardware appliances are servers or devices that perform certain security functions within the networking environment.

Network Security
What We Do
Network security combines multiple layers of defences at the edge and in the network. Each network security layer implements policies.
Data security refers to the process of protecting data from unauthorized access and data corruption throughout its lifecycle & your personal data safe.
web security refers to the protective measures and protocols that organizations adopt to protect the organization from, cyber criminals.
A running commentary of text messages pertaining to one topic. Message threads are used in all forms of user discussions on the Internet.
Database security measures include authentication, the process of verifying if a user's credentials match those stored in your database.
Protection of data stored online via cloud computing platforms from theft, leakage & deletion and also Protect your cloud data and storage.
Network & Security
Network Security Advantages& Features

Network & Security
Linux Server Advantages& Features

Network & Security
Cloud Security Advantages & Features


